ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Photoemission Analysis
Detect photon emissions from your IC to observe its behavior during operation.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Code Audit & Verification
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Automotive
Security Lab
Gov. Agencies
Academics
Defense
Healthcare
Energy
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
esReverse featured on NIST Binary Code Scanners list
Our esReverse platform has been officially included on the NIST Binary Code Scanners list, underscoring our dedication to advancing the field of binary code scanning and security analysis.
But what qualifies a binary code scanner? What exactly is binary code scanning, and how does esReverse stand out as the best option?
What is a binary code scanner?
A binary code scanner is a sophisticated tool designed to analyse binary code, the low-level code that computers execute directly. Unlike source code, which is written in high-level programming languages, binary code is machine-readable and requires specialised tools for examination.
Binary code scanners are essential for identifying vulnerabilities, ensuring software security, and validating code integrity. These scanners perform several key functions:
- Vulnerability Detection: Identifies known and unknown security flaws within binaries.
- Malware Detection: Detects malicious code hidden within software.
- Compliance Checks: Ensures that software complies with security standards and regulations.
- Code Quality Assessment: Analyses the binary for potential issues that could affect performance or stability.
To maximise the effectiveness of binary code scanning, it is important to follow certain best practices. Regular scanning is essential for identifying new vulnerabilities as they emerge, ensuring that software remains secure over time. Additionally, adopting a layered approach by combining multiple tools can provide comprehensive coverage, as different tools often excel at identifying different types of issues.
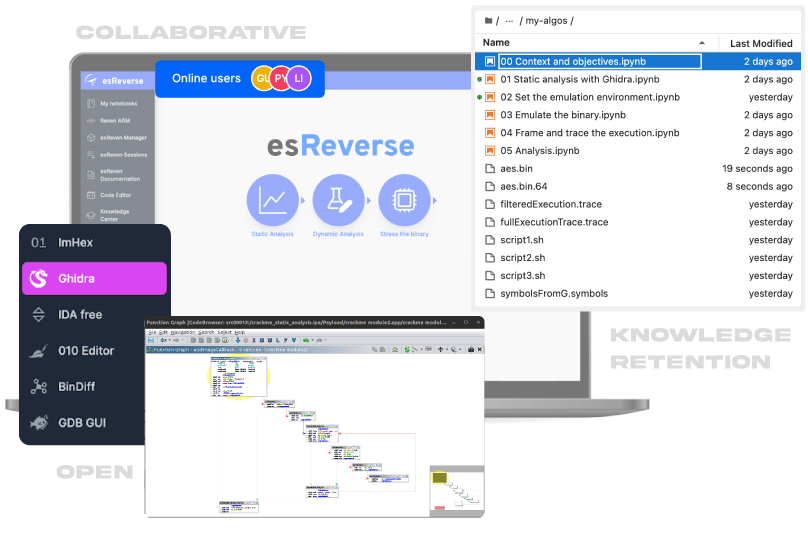
esReverse, the best binary code scanner solution
eShard’s esReverse is a powerful, collaborative platform dedicated to enhancing cybersecurity activities, including penetration testing, vulnerability research, code validation, and binary debugging.
🔵 Collaborative Environment
esReverse fosters a collaborative environment that significantly streamlines team workflows. By integrating JupyterLab notebooks, it enables team members to share insights and replay analyses at any point.
This feature enhances collaboration and ensures that knowledge is effectively distributed across the team, making it easier to tackle complex analysis tasks collectively. The ability to document, visualise, and share findings in a cohesive manner boosts productivity and ensures that everyone is on the same page.
🔵 Advanced Emulation Capabilities
One of the standout features of esReverse is its support for emulation across multiple architectures, including ARM, Intel, and RISC-V. This capability is crucial for conducting advanced dynamic analyses such as taint analysis and timeless analysis.
By simulating different environments, esReverse allows for a more thorough examination of binaries, identifying vulnerabilities and performance issues that might not be apparent through static analysis alone. This depth of analysis is essential for maintaining high security and performance standards in software development.
🔵 Advanced Testing and Analysis Tools
esReverse goes beyond basic scanning by incorporating advanced testing and analysis tools. Stress testing ensures that your binaries can withstand extreme conditions, providing confidence in their robustness. Fuzzing, another critical feature, identifies vulnerabilities by feeding random data into the software, revealing hidden flaws that might be exploited by attackers. Additionally, binary fault injection simulation tests how your software handles unexpected errors, ensuring that it can gracefully recover from or mitigate the impact of such events.
These advanced tools provide a comprehensive evaluation of your software’s resilience and security. All without leaving the platform.
🔵 Comprehensive Tool Integration
esReverse consolidates various powerful tools like Ghidra, IDA Pro and other powerful tools for binary analysis into a single environment. This integration eliminates the need to switch between different applications, thereby saving time and reducing the risk of errors.
The platform's flexibility and open architecture ensure easy interchangeability of tools, allowing users to customise their analysis environment according to their specific needs. This seamless integration of multiple tools enhances the overall efficiency and effectiveness of the binary code scanning process.
🔵 Access Expertise Effortlessly
With esReverse, accessing expertise is effortless thanks to our comprehensive library. This resource offers detailed information on complex software analysis topics, helping you and your team stay informed about the latest technologies and methodologies.
Our library includes executable and customizable use cases, tutorials, and theoretical notebooks, which are designed to bring your team up to speed efficiently. These resources ensure that your team can leverage the full potential of esReverse, enhancing their skills and knowledge in software analysis.
Conclusion
Binary code scanners are indispensable tools in the fight against software vulnerabilities and malware. While many tools are available, esReverse stands out as the best solution to help secure software binaries and protect against emerging threats.
Now that we have been included in the NIST Binary Code Scanners list, we hope to help even more cybersecurity experts enhance their efforts and safeguard their systems with confidence.
