ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Security Failure Analysis
Explore photoemission and thermal laser stimulation techniques.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Malevolent Code Analysis
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Security Labs
Governmental agencies
Academics
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
eShard releases a new Expertise Module for Lightweight Cryptography
Lightweight cryptography refers to cryptographic algorithms and protocols specifically designed for environments where resources are limited or where performance is the priority, such as in embedded systems or IoT or connected devices. These environments often have constraints in terms of processing power, memory, and energy consumption, which traditional cryptographic solutions might not adequately address.
Lightweight cryptographic methods aim to provide secure communication and data protection while being efficient in their use of computational resources. They are crucial in enabling secure communications in increasingly connected, yet resource-constrained, modern digital landscapes. Their development and implementation are essential for ensuring the security of small-scale devices that form the backbone of numerous everyday applications, from smart home devices to industrial control systems. Many algorithms have been designed for that purpose, including ASCON.

ASCON is a family of authenticated encryption and hashing algorithms designed primarily for lightweight applications. ASCON was one of the winners in the CAESAR competition (Competition for Authenticated Encryption: Security, Applicability, and Robustness), a global initiative aimed at identifying secure and efficient authenticated encryption schemes. More recently, it was selected by the NIST as a new standard for lightweight cryptography.
As a result, developers and experts must stay aligned with ongoing research. The selection of the right implementation has become crucial for many organizations. This necessitates swiftly gaining expertise in comprehending the new algorithms and their variations, understanding attack vectors and trends, and ultimately making informed implementation choices that align with the capabilities of the final devices.
To make the right decisions, many stakeholders must make sure to develop the internal expertise in-house. The topic is too critical to outsource the decisions that will have impacts for many years. It is with this mindset that eShard developed a dedicated base of theoretical and practical knowledge in a new LWC module with several objectives. We are proud to release the first version of the LWC module in January 2024.
What does this release provide?
The primary goal of this module is to bring the necessary knowledge for the understanding of ASCON and its implementations, such as the sponge construction The ASCON teams were aware of the side channel and the fault injection risk while designing it, and they made some decisions to facilitate the implementation of the side-channel countermeasure. This module includes a representative implementation in C and assembly language to elucidate ASCON operational principles and is the source of the dataset created.
The second goal of this module is to provide a clear view of the side-channel and fault attacks on ASCON together with the existing protected implementation. This will help users understand possible threats and existing protections. Typically, Correlation Power Analysis (CPA) can be applied to ASCON.
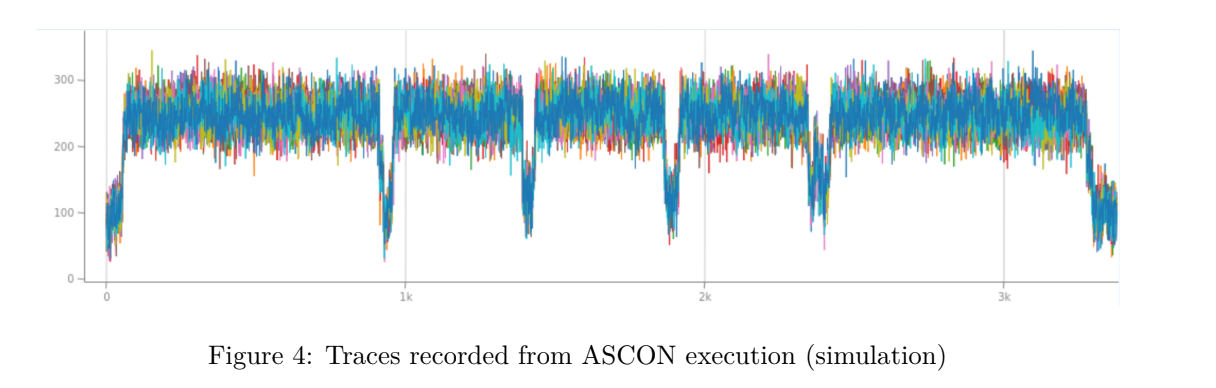
Our third goal is to provide datasets in order to put side-channel characterizations and attacks into practice. For this purpose, we have used our emulation environment executed on an ARM target. Our approach was to generate datasets that are highly exploitable, with the aim to provide an accurate representation of data involved in code execution. These datasets serve as material for our fourth and ultimate goal; a series of attack notebooks, where the different attack targets and related techniques are explained in detail.
Through tutorials, how-to’s and use cases Python notebooks, we provide reusable and editable support to address efficiently attacks and characterization methods applied on ASCON the LWC candidates selected for the NIST LWC Standard to appear...
To complete this release, we’ve investigated the practicality of the attacks on a microcontroller: a ST Microelectronic chip STM32 NUCLEO. For this, we loaded a non secure implementation of ASCON and performed the attack back to back, including the research of leakage areas and the exploitation on a real data set.
And the result represents a unique source of technical material for anyone willing to build in-house expertise in the complex field of strong Lightweight Cryptography:
-
✅ The module with mathematical knowledge for understanding the new algorithms concepts,
-
✅The module with data sets for experimenting the security analyses,
-
✅ The module with attack techniques and leakage analyses for developing the in-house expertise and challenging existing implementations,
-
✅ The built in use case on microcontrollers with every step explained in notebooks that can be replayed in-house on the same hardware device.
From day 1, the LWC module can be delivered to any users of the esDynamic platform. It therefore takes benefit of the key features that have made its success in the community of experts: open, flexible and collaborative. All the technical contents provided in this module aimed at helping our customers to manage their internal expertise and reaching a good level of know-how in the field of LWC secure implementation.

